What Cloud Marketplaces Do and Don’t Do
Not long ago, we observed here in our blog that the critical insights that drive business value come from data that is both (1) fast and (2) reliable.

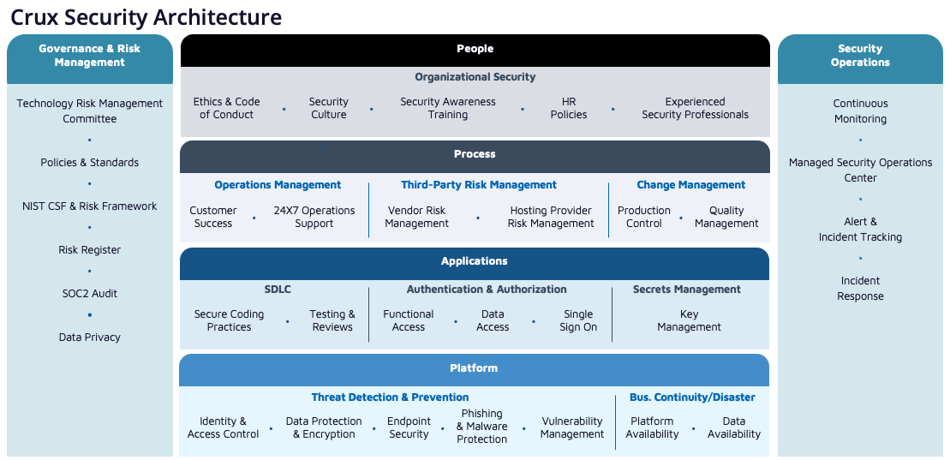
Industry leading security program designed to future-proof client infrastructure and Crux Platform - AICPA’s SOC2 Type II. Trust and security have been core tenets of the Crux platform since inception.
In our role as stewards of supplier and client data, we are committed to the protection of all data, information and systems under our management for our clients, suppliers, and partners.
Crux has developed a highly secure cloud native platform with a container based microservices architecture, to ingest, transform and deliver data. A robust information security management system (ISMS) based on the National Institute of Standards and Technology (NIST) Cybersecurity Framework is used to protect the platform. A dedicated Chief Security Officer (CSO) is responsible for technology risk management, security operations and oversight.
Crux implements a multi-faceted defensive barrier to identify malicious activity and proactively mitigate threats. This includes identity and access control, data protection, endpoint security, phishing and malware defense, change control, vulnerability management, and recurring employee training. A resilient architecture provides high availability of data and services, supported and tested with a disaster recovery plan and procedures. A 24x7 security operations center provides continuous security monitoring enabling rapid and consistent response to any security alerts and incidents.
Crux has attained AICPA’s SOC2 Type II attestation regarding the security and availability controls implemented for delivery of our services. These investments demonstrate Crux’s commitment to providing an inherently secure data delivery platform.
Case Study - Log4j Vulnerability:
Successfully detected and protected 100% of Crux platform and client pipeline from highest risk level exposure
On Dec. 9, 2021, a flaw in the code of a commonly used software library (Apache Log4j 2) built on the Java programming language was identified as being exploited. The zero-day vulnerability allowed attackers to execute a malicious payload on an affected system. It is estimated to be present in over a 100 million instances globally, and was given the highest severity rating (10) on the Common Vulnerability Scoring System due to its widespread prevalence, the high impact of an attack against it, and evidence that malicious actors are actively targeting organizations.
In response, Crux launched an immediate and complete review of all platform components. Within the first day we confirmed that due to our security architecture no vulnerable components were exposed or accessible externally. A remediation of all internal components was completed within days. During this time and subsequently, the Crux Security team monitored the platform for signs of malicious activity from common post-exploit sources along with vulnerability scans for any signs of exposure.
Crux’s multi-layer security, the container-based segmented-network architecture and a robust monitoring and response process enabled Crux to respond promptly and effectively to this severe threat, protecting our client’s data supply chain from exposure. Data suppliers benefit from the built-in security of the Crux platform in cloud based delivery of their datasets.
Takeaway: Adding Crux to the supply chain enhances the security of both the suppliers and consumers
To learn more about Crux and its data engineering and operations offering, contact us .

Not long ago, we observed here in our blog that the critical insights that drive business value come from data that is both (1) fast and (2) reliable.

This past year has been exciting, representing the dawning of a new age for artificial intelligence (AI) and machine learning (ML)—with large...

How do you get white-glove customer service from a major data supplier?